Although the Linux system is said to be least prone to malware and viruses, third-party applications may also not cause any trouble. But wait! The Linux systems are most safe and least vulnerable operating systems, but this doesn’t mean that it won’t get affected by anything at any time; it could be affected by non-trusted apps, third-party apps, etc. To protect the Linux system from the negative effect of these non-trusted apps, there is one way out, run up the non-trusted apps in an isolated container Sandbox. This Sandboxing of the apps prevents the system information and data from being utilized and protects the whole system from being affected by malware, virus, etc. Now the thought might be coming to your mind, i.e., how could you also use Sandbox apps on Linux, don’t bother, as we have written about the whole method in this article, and you have to read it all to know about it. Also Read: 10 Best Open Source Linux Media Players
How to Sandbox Non-trusted Apps in Linux Systems
The method is a little technical, and you should be sound to easily judge the non-trusted apps that can endanger your security in the Linux system. So have a look at the step-by-step guide below to proceed. Also Read: Reasons Why Hackers Prefer to Use Linux OS
Steps to Sandbox Non-trusted Apps on Linux Systems:
Download the “Firejail” on your Linux. To do that on Debian Ubuntu/Linux Mint open up the Terminal inside the OS and then type up the following command: Now enter your account password when asked and press enter. For confirmation, if asked, type up the key ‘y’ and press the enter key again. This will start up the installation process of the Firejail automatically but check that you are running active internet on your system unless you cannot get any results, and installation won’t be done. For any RedHat or Fedora-based distro of Linux, then use up the below command for downloading the Firejail and follow up the same procedure:
After you have downloaded the Firejail file just locate it from the terminal by the command “cd~/Downloads“. Install up the file from the package file by running up the command: “sudo dpkg –i firetools*.deb“. Fill up your password if prompted and then press the enter key.
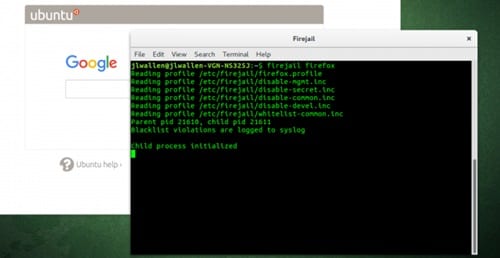
Now, if you want to run any installed application inside the Firejail or just run it by sandboxing, then run up the below command in the terminal. ” firejail app_name” for example ” firejail firefox” command, will run up the Firefox web browser in sandbox mode. This will restrict that particular app from accessing your directories and files. Still, if you aren’t happy with the restrictions that the above mode provides and want to run up the apps in much more private mode, then do that by running up the command :
Still, if you aren’t happy with the restrictions that the above mode provides and want to run up the apps in much more private mode, then do that by running up the command : “firejail appname –private“, for example “firejail firefox –private” command, will run the firefox web browser in a completely restricted mode where it cannot access even the small data from your device directories.
This can be done all through the commands, but if you want to perform the same actions in GUI mode then or in a software-like platform, then you can do that by typing up the command “firetools” and you will see software running on your screen through which you can perform up the similar actions as described above but not using up the commands but through simple surfing method. Also Read: Great Linux Design Tools Digital Artists Should Know This was all ways through which you could easily run up the non-trusted apps in the sandbox on your Linux and protect your device from the threats that these apps could probably cause. You should also run up the web browsers and other online apps in sandbox mode as these apps could be most vulnerable as there is a transfer of data between your system and servers, and the virus and malware are all transferred through this way only!